dnsx:快速、多用途DNS工具包,专为运行DNS查询而设计
dnsx是一款快速且用途广泛的 DNS 工具包,旨在通过retryabledns库运行各种探测。它支持多个 DNS 查询、用户提供的解析器、DNS 通配符过滤(如shuffledns)等。
Github:https://github.com/projectdiscovery/dnsx/
特征
- 用于查询 DNS 记录的简单方便的实用程序
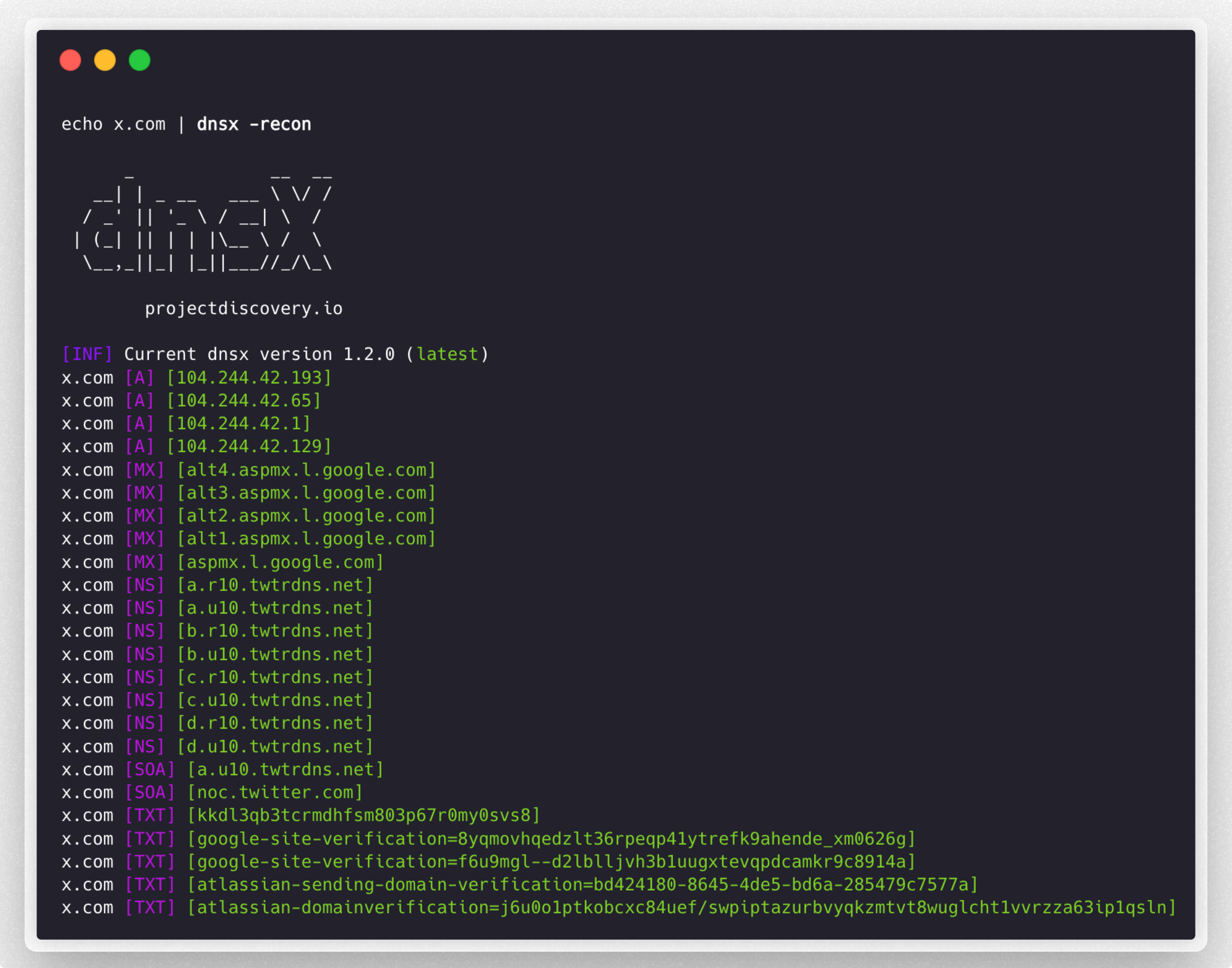
- 支持 A, AAAA, CNAME, PTR, NS, MX, TXT, SRV, SOA 记录查询
- 支持DNS解析/暴力破解
- 支持自定义解析器输入
- 支持 (TCP/UDP/DOH/DOT) 多种解析器格式
- 支持标准输入和标准输出
- 支持自动通配符处理支持
安装说明
dnsx需要go1.21才能成功安装。运行以下命令安装最新版本:
go install -v github.com/projectdiscovery/dnsx/cmd/dnsx@latest用法
dnsx -h这将显示该工具的帮助。以下是它支持的所有开关。
INPUT:
-l, -list string list of sub(domains)/hosts to resolve (file or stdin)
-d, -domain string list of domain to bruteforce (file or comma separated or stdin)
-w, -wordlist string list of words to bruteforce (file or comma separated or stdin)
QUERY:
-a query A record (default)
-aaaa query AAAA record
-cname query CNAME record
-ns query NS record
-txt query TXT record
-srv query SRV record
-ptr query PTR record
-mx query MX record
-soa query SOA record
-any query ANY record
-axfr query AXFR
-caa query CAA record
-recon query all the dns records (a,aaaa,cname,ns,txt,srv,ptr,mx,soa,axfr,caa)
-e, -exclude-type value dns query type to exclude (a,aaaa,cname,ns,txt,srv,ptr,mx,soa,axfr,caa) (default none)
FILTER:
-re, -resp display dns response
-ro, -resp-only display dns response only
-rc, -rcode string filter result by dns status code (eg. -rcode noerror,servfail,refused)
PROBE:
-cdn display cdn name
-asn display host asn information
RATE-LIMIT:
-t, -threads int number of concurrent threads to use (default 100)
-rl, -rate-limit int number of dns request/second to make (disabled as default) (default -1)
UPDATE:
-up, -update update dnsx to latest version
-duc, -disable-update-check disable automatic dnsx update check
OUTPUT:
-o, -output string file to write output
-j, -json write output in JSONL(ines) format
-omit-raw, -or omit raw dns response from jsonl output
DEBUG:
-hc, -health-check run diagnostic check up
-silent display only results in the output
-v, -verbose display verbose output
-raw, -debug display raw dns response
-stats display stats of the running scan
-version display version of dnsx
-nc, -no-color disable color in output
OPTIMIZATION:
-retry int number of dns attempts to make (must be at least 1) (default 2)
-hf, -hostsfile use system host file
-trace perform dns tracing
-trace-max-recursion int Max recursion for dns trace (default 32767)
-resume resume existing scan
-stream stream mode (wordlist, wildcard, stats and stop/resume will be disabled)
CONFIGURATIONS:
-auth configure projectdiscovery cloud (pdcp) api key (default true)
-r, -resolver string list of resolvers to use (file or comma separated)
-wt, -wildcard-threshold int wildcard filter threshold (default 5)
-wd, -wildcard-domain string domain name for wildcard filtering (other flags will be ignored - only json output is supported)运行 dnsx
DNS 解析
从各种来源获得的被动子域名列表中过滤活动主机名:
subfinder -silent -d hackerone.com | dnsx -silent
a.ns.hackerone.com
www.hackerone.com
api.hackerone.com
docs.hackerone.com
mta-sts.managed.hackerone.com
mta-sts.hackerone.com
resources.hackerone.com
b.ns.hackerone.com
mta-sts.forwarding.hackerone.com
events.hackerone.com
support.hackerone.com打印输出给定子域名列表的A记录:
subfinder -silent -d hackerone.com | dnsx -silent -a -resp
www.hackerone.com [104.16.100.52]
www.hackerone.com [104.16.99.52]
hackerone.com [104.16.99.52]
hackerone.com [104.16.100.52]
api.hackerone.com [104.16.99.52]
api.hackerone.com [104.16.100.52]
mta-sts.forwarding.hackerone.com [185.199.108.153]
mta-sts.forwarding.hackerone.com [185.199.109.153]
mta-sts.forwarding.hackerone.com [185.199.110.153]
mta-sts.forwarding.hackerone.com [185.199.111.153]
a.ns.hackerone.com [162.159.0.31]
resources.hackerone.com [52.60.160.16]
resources.hackerone.com [3.98.63.202]
resources.hackerone.com [52.60.165.183]
resources.hackerone.com [read.uberflip.com]
mta-sts.hackerone.com [185.199.110.153]
mta-sts.hackerone.com [185.199.111.153]
mta-sts.hackerone.com [185.199.109.153]
mta-sts.hackerone.com [185.199.108.153]
gslink.hackerone.com [13.35.210.17]
gslink.hackerone.com [13.35.210.38]
gslink.hackerone.com [13.35.210.83]
gslink.hackerone.com [13.35.210.19]
b.ns.hackerone.com [162.159.1.31]
docs.hackerone.com [185.199.109.153]
docs.hackerone.com [185.199.110.153]
docs.hackerone.com [185.199.111.153]
docs.hackerone.com [185.199.108.153]
support.hackerone.com [104.16.51.111]
support.hackerone.com [104.16.53.111]
mta-sts.managed.hackerone.com [185.199.108.153]
mta-sts.managed.hackerone.com [185.199.109.153]
mta-sts.managed.hackerone.com [185.199.110.153]
mta-sts.managed.hackerone.com [185.199.111.153]提取给定子域名列表的A记录:
subfinder -silent -d hackerone.com | dnsx -silent -a -resp-only
104.16.99.52
104.16.100.52
162.159.1.31
104.16.99.52
104.16.100.52
185.199.110.153
185.199.111.153
185.199.108.153
185.199.109.153
104.16.99.52
104.16.100.52
104.16.51.111
104.16.53.111
185.199.108.153
185.199.111.153
185.199.110.153
185.199.111.153提取给定子域名列表的CNAME记录:
subfinder -silent -d hackerone.com | dnsx -silent -cname -resp
support.hackerone.com [hackerone.zendesk.com]
resources.hackerone.com [read.uberflip.com]
mta-sts.hackerone.com [hacker0x01.github.io]
mta-sts.forwarding.hackerone.com [hacker0x01.github.io]
events.hackerone.com [whitelabel.bigmarker.com]提取给定子域名列表的ASN记录:
subfinder -silent -d hackerone.com | dnsx -silent -asn
b.ns.hackerone.com [AS13335, CLOUDFLARENET, US]
a.ns.hackerone.com [AS13335, CLOUDFLARENET, US]
hackerone.com [AS13335, CLOUDFLARENET, US]
www.hackerone.com [AS13335, CLOUDFLARENET, US]
api.hackerone.com [AS13335, CLOUDFLARENET, US]
support.hackerone.com [AS13335, CLOUDFLARENET, US]使用DNS 状态代码对给定的(子)域名列表进行探测:
subfinder -silent -d hackerone.com | dnsx -silent -rcode noerror,servfail,refused
ns.hackerone.com [NOERROR]
a.ns.hackerone.com [NOERROR]
b.ns.hackerone.com [NOERROR]
support.hackerone.com [NOERROR]
resources.hackerone.com [NOERROR]
mta-sts.hackerone.com [NOERROR]
www.hackerone.com [NOERROR]
mta-sts.forwarding.hackerone.com [NOERROR]
docs.hackerone.com [NOERROR]使用查询从给定的网络范围中提取子域名PTR:
echo 173.0.84.0/24 | dnsx -silent -resp-only -ptr
cors.api.paypal.com
trinityadminauth.paypal.com
cld-edge-origin-api.paypal.com
appmanagement.paypal.com
svcs.paypal.com
trinitypie-serv.paypal.com
ppn.paypal.com
pointofsale-new.paypal.com
pointofsale.paypal.com
slc-a-origin-pointofsale.paypal.com
fpdbs.paypal.com使用查询从给定的 ASN 中提取子域名PTR:
echo AS17012 | dnsx -silent -resp-only -ptr
apiagw-a.paypal.com
notify.paypal.com
adnormserv-slc-a.paypal.com
a.sandbox.paypal.com
apps2.paypal-labs.com
pilot-payflowpro.paypal.com
www.paypallabs.com
paypal-portal.com
micropayments.paypal-labs.com
minicart.paypal-labs.comDNS暴力破解
使用 d 和 w 标志为给定域或域列表强制创建子域名:
dnsx -silent -d facebook.com -w dns_worldlist.txt
blog.facebook.com
booking.facebook.com
api.facebook.com
analytics.facebook.com
beta.facebook.com
apollo.facebook.com
ads.facebook.com
box.facebook.com
alpha.facebook.com
apps.facebook.com
connect.facebook.com
c.facebook.com
careers.facebook.com
code.facebook.com暴力破解使用单个或多个关键字输入锁定子域名,因为 d 或 w 标志支持文件或逗号分隔关键字输入:
dnsx -silent -d domains.txt -w jira,grafana,jenkins
grafana.1688.com
grafana.8x8.vc
grafana.airmap.com
grafana.aerius.nl
jenkins.1688.com
jenkins.airbnb.app
jenkins.airmap.com
jenkins.ahn.nl
jenkins.achmea.nl
jira.amocrm.com
jira.amexgbt.com
jira.amitree.com
jira.arrival.com
jira.atlassian.net
jira.atlassian.com所有输入类型("列表"、"域名"、"字表")都接受来自标准输入的值。-list标志默认为标准输入,但其他输入类型也可以通过添加"-"(破折号)作为参数来实现:
cat domains.txt | dnsx -silent -w jira,grafana,jenkins -d -
grafana.1688.com
grafana.8x8.vc
grafana.airmap.com
grafana.aerius.nl
jenkins.1688.com
jenkins.airbnb.app
jenkins.airmap.com
jenkins.ahn.nl
jenkins.achmea.nl
jira.amocrm.com
jira.amexgbt.com
jira.amitree.com
jira.arrival.com
jira.atlassian.net
jira.atlassian.com使用基于占位符的单词表进行 DNS 暴力破解
$ cat tld.txt
com
by
de
be
al
bi
cg
dj
bsdnsx -d google.FUZZ -w tld.txt -resp
_ __ __
__| | _ __ ___ \ \/ /
/ _' || '_ \ / __| \ /
| (_| || | | |\__ \ / \
\__,_||_| |_||___//_/\_\ v1.1.2
projectdiscovery.io
google.de [142.250.194.99]
google.com [142.250.76.206]
google.be [172.217.27.163]
google.bs [142.251.42.35]
google.bi [216.58.196.67]
google.al [216.58.196.68]
google.by [142.250.195.4]
google.cg [142.250.183.131]
google.dj [142.250.192.3] 通配符过滤
dnsx 的一大特点是能够处理基于 DNS 的多级通配符,而且只需极少的 DNS 请求即可完成。有时,所有子域名都会解析,这会导致输出中出现大量垃圾。dnsx处理这种情况的方法是跟踪有多少个子域名指向一个 IP,如果子域名的数量增加超过某个阈值,它就会在该 IP 的所有主机级别上反复检查通配符。
dnsx -l subdomain_list.txt -wd airbnb.com -o output.txtDnsx 作为库
您可以在 golang 程序中直接使用该库。以下代码片段是 golang 程序中的使用示例。请参阅此处了解详细的包配置和使用方法。
package main
import (
"fmt"
"github.com/projectdiscovery/dnsx/libs/dnsx"
)
func main() {
// Create DNS Resolver with default options
dnsClient, err := dnsx.New(dnsx.DefaultOptions)
if err != nil {
fmt.Printf("err: %v\n", err)
return
}
// DNS A question and returns corresponding IPs
result, err := dnsClient.Lookup("hackerone.com")
if err != nil {
fmt.Printf("err: %v\n", err)
return
}
for idx, msg := range result {
fmt.Printf("%d: %s\n", idx+1, msg)
}
// Query
rawResp, err := dnsClient.QueryOne("hackerone.com")
if err != nil {
fmt.Printf("err: %v\n", err)
return
}
fmt.Printf("rawResp: %v\n", rawResp)
jsonStr, err := rawResp.JSON()
if err != nil {
fmt.Printf("err: %v\n", err)
return
}
fmt.Println(jsonStr)
return
}📋 注释
- 默认情况下,dnsx检查A记录。
- 默认情况下,dnsx使用 Google、Cloudflare、Quad9解析器。
- 可以使用
r标志加载自定义解析器列表。 - 域名 (
wd) 输入必须用于通配符消除。 - 使用通配符过滤时不能使用 DNS 记录标记。
- DNS 解析 (
l) 和 DNS 强制 (w) 不能同时使用。 - VPN 运营商倾向于过滤高 DNS/UDP 流量,因此该工具可能会出现数据包丢失的情况


评论8次
暴力破解还得是配合字典。
收藏了,看中了这个暴力破解子域名功能
信息收集工具必须要下载 多个工具多条路 感谢大佬无私奉献
感谢分享
感谢分享 后面试试看
确实好用,作为工具互补很不错。
感谢分享
好东西 下载了 以备不时之需 补充弹药库